This live linux distro is a little bit different to the ones we've tried out up until now. This one has a very specific purpose, and it's to make a secure system which uses tor for practically all communications, and then forgets everything on shutdown. Tails itself is an acronym for "The Amnesiac Incognito Live System", where the "amnesia" refers to forgetting everything (there will be no browser history or work files stored on the PC itself) and the "incognito" refers to the use of tor. Obviously all the other live distros here fit the "amnesiac live system" requirement too, but most of the others here don't take steps in pursuit of anonymity.
Technically, it is currently based on Debian Stable (in the case of this 3.2 version, Debian Stretch), with a Gnome 3 desktop (although this doesn't say Gnome anywhere). Its main selling feature is the selection and configuration of the included applications, especially the torification and add-ons to Firefox.
This being the 21st Century, we don't deal with rewriteable DVDs any more, everything revolves around USB sticks, onto which the downloadable ISO can be installed. An 8 GB stick is recommended, but probably a 4 GB stick would also work, just without all the optional persistence features.
The bad news is, that if you haven't got linux already, then the procedure for getting a working Tails stick is twice as complex as you would expect. For example, from a Windows system, you download the iso and write it to a stick, then boot that stick and use it to write a second stick! Then you wipe the first stick and just use the second one. And if that sounds weird, then, well, yeah. Apparently there's some good reason somewhere why dd or unetbootin can't prepare the stick properly directly.
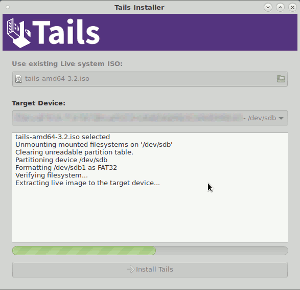
Fortunately, we have a linux system already (Debian Stretch), and so we get to use a shortcut method. We install the package tails-installer and then use that to write the USB stick, then you only need one stick instead of two. This gui is shown in the screenshot on the right.
Of course we've also got to get the ISO from somewhere, and the Tails home page lists a few ways of doing this. Most convenient is probably to download the torrent file, then as long as this small download hasn't been compromised, the torrent client will check the validity of the actual ISO. Once downloaded, you get a 1.2 GB tails-amd64-3.2.iso file, and a small signature file as .asc. So the idea is that you should be able to verify this signature to satisfy yourself that this ISO could only have been made by the Tails devs and hasn't been exchanged for a malicious image made by somebody else. The Tails site describes how to do this using gpg on the command line, but it's a bit of a chicken-and-egg problem, how can you trust which key belongs to the Tails devs? They can't just provide the key fingerprint by download, because trusting their downloads is something we want to confirm. So they suggest adding to your gpg keyring the key of one of the Debian developers and ask you to trust him (and therefore all the keys he trusts). It seems a shame that they can't include the necessary verification inside the tails-installer package from the Debian archives, as we've already trusted that.
Anyway, assuming that we're now happy with the ISO, we fire up the tails-installer, point it at the ISO and the USB stick, and confirm that the whole stick will be wiped. After a few painless minutes, the stick is ready to be tested.
So here is Tails, looking very businesslike with a plain Gnome desktop and the tor browser.
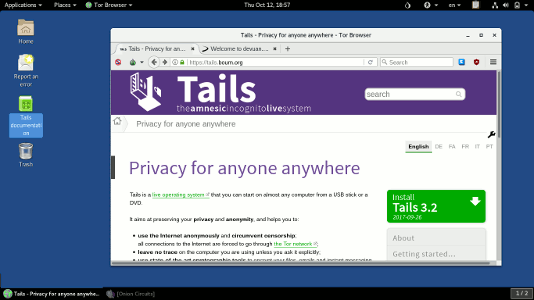
There's no 'footprint' icon in the start menu to tell you it's Gnome, but there is an "Applications" menu in the topleft, and a hidden sidebar which appears when you move the cursor into the top-left corner of the screen. Another thing worth noting is that each application window (such as the Tor browser shown in this screenshot) doesn't have a menu bar at the top. It seems they've copied Apple's approach of moving that menu out of the window and putting it in the top title bar (here inside the "Tor Browser" dropdown next to "Places").
There's a workspace switcher in the bottom right, which oddly shows "1/1" when no windows are open and "1/2" when one or more is open. For those already familiar with the Gnome desktop, this should all be pretty standard stuff.
At the time of writing, this Tails version 3.2 is based on Debian Stretch (Stable), but there are plans to transition to tracking Debian Testing instead in future.
A big draw of Tails is the included applications, and most importantly this includes Firefox, rebranded as "Tor Browser" and configured with additional security measures. These include forcing all browser traffic through Tor, and applying add-ons such as https everywhere, noscript, torbutton and ublock origin. It uses version 52.4 which is the latest version packaged for Debian. For non-browser-based communication you've also got Thunderbird (for email), Pidgin (for Instant Messaging) and Gobby (a multiplayer text editor), and again these will use Tor for their traffic too.
After booting, and after connection to the internet, the connections to the Tor network are initialised. This takes some time, for the selection of the Tor nodes, exchange of transport keys and establishing of Tor circuits. Once this is done, a notification appears at the top of the screen:

Note that if you're using a wireless network connection with a password, Tails (being amnesiac) will forget the password every shutdown, so you'll need to keep typing it in after every boot. Unless of course you use the persistence feature, described below.
It's slightly less clear why the Tails developers would choose to include some of the other applications, like Gimp, Inkscape, Scribus and Audacity. I mean, they're all great applications, and potentially useful, but are they needed on such a distro? Perhaps there is a use case for people wanting to anonymously use Gimp and Inkscape?
Interestingly, this Tails image reports its version as "Tails 3.2, live-build:3.0.5+really+is+2.0.12". So is it 3.2, or 3.0.5, or 2.0.12?
It's a conundrum. The Tails devs obviously put a lot of emphasis on its "amnesiac" properties, and one can well see that having a PC on which there are absolutely no traces of recent Tails sessions could be very desirable. However, one can also well understand that not everything can be conveniently stored online and maybe having somewhere to save things locally would be useful too. So what Tails offers is the option to add an encrypted partition to the Tails stick, protected with a password, where you can keep some things persistent, and then lets you choose which things should get persisted and which not.
So if you do choose to create such a partition, you're losing (some of) the amnesiac properties of Tails, and you have the inconvenience of having to type in that password on every boot of Tails if you want to use it. If someone gets hold of your stick, they can immediately see that there's an encrypted partition on there, and if they know the password they can mount the partition and read everything. Presumably it wouldn't be too difficult to clone the whole stick and brute force the password if necessary.
If you don't use this persistence feature, and you lose the stick, then all that person gains is a fresh copy of Tails, with nothing to say whether it had actually ever been used or not, or what for.
Tails has an interesting approach to its users and passwords. There's no password to login, which is fine because being amnesiac, there's nothing to protect. But by default the root user is completely disabled, which means that even sudo isn't available. The reasoning goes that if by some chance your user account got compromised by a remote attacker, they couldn't escalate it to a root-level compromise because there isn't a root user at all.
So there may be good security reasons for disabling all of root, but it does mean that without sudo you can't install new packages, can't update existing packages, and can't even update the list of packages. If you want to do any of those things, you'll need to click on the "+" button on the startup options dialog and choose an "additional option" of enabling the root user with a chosen password. But of course that choice of password only applies to the current session, if you reboot Tails then it will have forgotten everything again (obviously).
As mentioned earlier, this version of Tails is based on Debian Stable, so there shouldn't be a huge number of packages being updated, it should all be more or less 'stable'. But if I do choose to do a regular upgrade on this Tails, it already recommends dozens of package upgrades, many of which sound like they could be important. These currently include packages like tor, gpg, Kerberos, haveged and SELinux, all of which without root access can't be upgraded.
If you find yourself regularly using Tails and regularly needing additional packages, you can combine the root account enabling with the persistence features, and store the extra packages inside the (encrypted) stick partition. This would mean that they don't have to be downloaded additionally for each session, but of course the more you tweak the persistence options, the less of its carefully designed protections Tails can give you.
As it is, it's a very usable Debian-based distro, it's quick to boot and smooth to run. But that's not why you'd choose it over other, Debian-based distros. It's designed to meet a specific need, for those who want or need easy-to-use obfuscation of their communications. And doubtless it draws attention (and suspicion) to the user, as it is obvious that tor is being used and perhaps obvious that Tails is being used. The Tails documentation mentions that this is technically possible but that as far as possible all Tails users look alike.
So is Tails only for criminals to use, to hide their illegal (and probably disgusting) browser traffic? No, not at all. There is nothing illegal or immoral about using Tails, or using Tor. And in fact the more completely innocent, inane and meaningless traffic going over Tor the better. But to be a user of Tails you'd have to have at least a passing interest in the possibilities of communicating privately and browsing anonymously.
But there are some things that you wouldn't necessarily want to do using Tails. Running BitTorrent is one example which sounds like a good idea but according to the Tor developers really isn't. Similarly, would you want to access your gmail (entering your name and password to Google) while simultaneously broadcasting to them that you're using Tails? There are lots of other ways you can identify yourself from your browsing, even if you do it through tor. And you can't even edit Wikipedia while using Tails, because Wikipedia now prevents edits and user creation if the request looks like it came from tor.
So if you're interested in using Tails and Tor, but not use it for everything, then you're going to have to think about two separate systems and some way to make sure they're separate, which is probably not so easy. But for sure it's an interesting experiment and Tails provides a very easy way to try out Tor and its associated applications.
Wikipedia has limited information at Tails_(operating_system) and Tor_(anonymity_network), and the main Tails home page is at tails.boum.org. Also you might be able to find some useful information on tor-related discussion forums like tor.stackexchange or reddit.